Organizations relying on legacy IBM i applications to drive critical operations are facing significant challenges in securing the platform’s longevity. Addressing security vulnerabilities has become vital as these applications age, especially in the face of rising cybersecurity threats. Another pressing concern is modernizing the user experience to meet evolving user expectations, as interfaces built decades ago now feel obsolete, despite the platform’s proven stability and reliability.
Furthermore, as experienced IBM i experts retire, companies risk losing vital institutional knowledge that could undermine their age-old assets. Considering these hurdles, forward-looking organizations are committed to modernizing their IBM i infrastructure, making sure it not only survives but continues to drive innovation across their operations. In this blog, we will deep dive into how businesses can build future-ready strategies to secure their IBM i applications for the long term. The post also delves into the key benefits of modernizing IBM i applications.
Table of Contents
Foolproof Ways to Secure IBM i Applications
- Embracing a Blended Application Strategy
- Creating a Blended Architecture
- Fortifying Security Defenses
- IV. Modernizing with APIs
- V. Honing New Skills
Foolproof Ways to Secure IBM i Applications
Keeping your IBM i applications safe and up to date is easier than you think. These tried-and-tested strategies help protect your applications while preparing for what’s next. Here’s how to make your IBM i applications secure for years to come.
I. Embracing a Blended Application Strategy
Today, companies are increasingly adopting a “blended” application strategy to modernize their IBM i applications and harness the power of new technologies. So, while they continue to use the existing RPG, COBOL, and DB2 code for running core applications, they are incrementally introducing modern technologies to enhance functionality and user experience.
By pursuing a blended approach, businesses continue to benefit from the reliability, user-friendliness, and low cost of ownership of the IBM i technology, while simultaneously leveraging the capabilities of emerging technologies.
As a part of this strategy, companies are considering IBM i application modernization, making it easier to onboard new skilled developers to work on their applications. This also eliminates the risks associated with migrating to a completely new platform, saving on their hard-earned investments.
II. Creating a Blended Architecture
To support the ‘blended’ approach mentioned above, organizations require an architecture that allows different technologies to communicate seamlessly. If they introduce modern user interfaces or incorporate open-source modules built using languages such as JavaScript, C#, PHP, or Swift, they require an interface layer capable of translating between communication protocols of these languages and the requirements of IBM i.
The key to achieving this integration lies in embracing a loosely coupled architecture, ensuring that changes on either the open-source or the IBM i side do not disrupt the overall system’s functionality. This is where an API-driven structure shines since it provides a robust foundation for secure, authenticated, and efficient data exchange and routing.
APIs act as intermediaries, governed by well-defined “contracts” that specify the required input data fields and the expected responses. However, this loosely coupled API structure must be bidirectional, supporting both inbound requests from external applications to the IBM i, as well as outbound calls from the IBM i to other platforms and services in the broader ecosystem. This bidirectional capability ensures your IBM i remains a fully integrated and collaborative component within your organization’s digital landscape.
III. Fortifying Security Defenses
Implementing modern-day security measures can safeguard your IBM i applications from both external and internal threats. Several organizations using IBM i still rely on basic authentication, an old-school identity verification method wherein the user is instructed to provide a username and password before they can be granted access to a resource (IBM i application in this case). Such an approach is regarded risky as it involves a higher probability of data theft. Organizations can consider using encrypted JSON web tokens to secure their transmissions, OAuth (Open Authorization) for validating user identity, and multi-factor authentication to provide an additional layer of protection.
“Security is no longer optional—future-proofing IBM i requires encryption, multi-factor authentication, and regular audits.” – Pete Massiello, IBM i Expert
Besides, open-source security modules written in languages such as Python and JavaScript can be leveraged to implement advanced security capabilities. These modules, used by thousands across the globe, are updated constantly by security professionals. So, if any vulnerability is detected, it can be addressed swiftly. The best part is that most of these modules can be freely downloaded from the internet and incorporated into your IBM i environment.
The Ultimate Guide to Migrating IBM i Applications to the Cloud
IV. Modernizing with APIs
Embracing a loosely coupled API architecture can enhance your ability to leverage the latest UI/UX technologies. It simplifies the modernization of your codebase by seamlessly integrating open-source modules with your existing RPG/COBOL code using high-speed connections.
By utilizing modern UI frameworks like Angular, React, and Vue, you can efficiently build user interfaces for IBM i applications. These frameworks allow you to incorporate open-source UI components easily. Need a dropdown list or want to export data to Excel? Simply download the necessary code, there’s no need to write the code from scratch. For even greater simplicity, you can use low-code tools, feeding them data from your IBM i applications.
The primary challenge of IBM i applications modernization using APIs lies in the monolithic nature of IBM i programs. IBM i programs with hundreds and thousands of lines of code are not uncommon. These monolithic applications make it challenging to extract individual functions for API enablement. To overcome this, IBM i users are increasingly moving to open-source languages with built-in modules to enhance their applications.
“Modernizing IBM i applications with APIs and cloud connectivity ensures they remain relevant in a digital-first world.” – Allison Butterill, IBM i Product Offering Manager
IBM i users can now write new functions in open-source languages such as Python, JavaScript, and C# and use APIs to call these functions from their IBM i application. High-speed APIs facilitate this integration without slowing down IBM i processes. Users can also add email and text messaging, QR code scanning, and e-commerce capabilities to applications using free, open-source modules. They can also replace existing functions in IBM i programs with componentized open-source code. High-speed APIs enable you to decompose existing monolithic applications into components that can support emerging technologies.
V. Honing New Skills
This is possibly the most crucial yet challenging step in ensuring the longevity of your IBM i applications . Future-proofing IBM i demands an aggressive approach to continuous learning and embracing new technologies. Instead of responding to problems that necessitate change, businesses should proactively seek opportunities by leveraging the latest technologies to drive change. For instance, they can learn and experiment with new programming languages such as Python and JavaScript and explore the possibilities they offer for IBM i applications modernization.
Organizations can encourage IBM i developers to adopt open-source development tools, such as Git, Jenkins, and Visual Studio Code, as promoted by IBM’s MERLIN initiative. Such a step will enable them to seek the expertise of new developers familiar with these tools to enhance their IBM i environment.
While this proactive mindset may seem obvious, we have grown complacent, opting for familiar and comfortable choices for far too long. In some ways, IBM has enabled this complacency by maintaining backward compatibility, allowing many IBM i users to continue running legacy System/36 code. While this backward compatibility is a strength that sets IBM i apart, it has also inadvertently hindered our progress and innovation. If you want to truly future- proof your applications, you need to discard such short-sightedness and think long-term.
How RPG Programmers Help Businesses in IBM i App Development
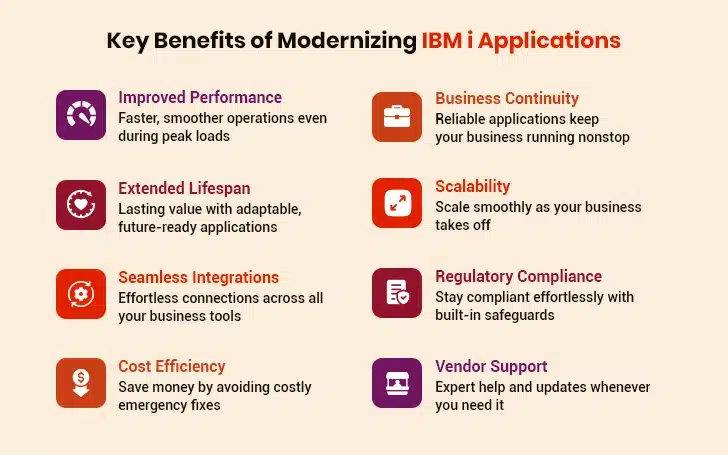
Key Benefits of Modernizing IBM i Applications
Modernizing your IBM i applications means less trouble later. These benefits show how preparing today helps avoid costly fixes tomorrow while keeping your business moving forward without interruptions.
1. Improved Performance
Upgraded IBM i applications work faster and handle more tasks at once. They process information quickly without slowing down during busy times. As a result, daily operations are completed in less time with fewer errors. The application also responds immediately when multiple people use it together, making teamwork easier. Furthermore, data moves smoothly between different applications, and old bottlenecks that caused delays get removed. Overall, regular updates maintain this good performance over time, adapting to growing business needs.
2. Extended Lifespan
Modernized IBM i applications stay useful for many years. Instead of becoming outdated quickly, updated applications can adapt to new requirements as they come. This means the business doesn’t have to replace everything suddenly, saving time and money. Staff can continue using tools they know well while still benefiting from improvements. The application also stays relevant because it can incorporate new features when needed. Furthermore, companies avoid the disruption of switching to completely new platforms before they’re ready. By keeping the IBM i up-to-date, businesses protect their investment and ensure their applications keep supporting operations effectively for a long time without unexpected overhauls.
3. Seamless Integrations
Updated IBM i applications connect easily with other software and tools. They can share information smoothly with different applications, making it easier to connect departments and workflows. As a result, data moves automatically between applications without manual work, reducing errors and saving time. Businesses can also add new services or platforms without complicated adjustments. Whether it’s cloud-based tools or mobile access, everything fits together properly. This flexibility allows companies to use the best solutions for each task while keeping everything connected. Employees get what they need without dealing with compatibility issues. Smooth integrations mean less frustration and more efficient work across the entire organization.
4. Cost Efficiency
Modernized IBM i applications save money in the long run. While updates require some investment, they prevent bigger expenses later. Older applications often need costly emergency fixes and consume more resources. Whereas, updated applications run more efficiently, reducing maintenance needs. As a result, staff spend less time solving technical problems, allowing them to focus on important work. Budgets also become more predictable because there are fewer unexpected repair costs. The money saved can be used for other business improvements instead of constantly patching old applications. Over time, these savings add up, making modernization a smart financial decision that pays off year after year.
5. Business Continuity
Modernized applications help prevent disruptions that could stop work unexpectedly. They have fewer crashes and recover faster when issues do occur. As a result, crucial operations keep running smoothly even during busy times or technical problems. Employees can also rely on the applications when needed. Furthermore, customers don’t also experience delays from technology failures. The business maintains its normal pace without unexpected pauses. This reliability gives everyone confidence that work can continue without major interruptions. Companies avoid the stress and costs that come with prolonged downtime situations.
6. Scalability
Updated IBM i applications can grow along with the business without causing problems. When a company needs to handle more work or users, the application adjusts smoothly. This simply means that businesses can take on new opportunities without worrying about their applications keeping up. Furthermore, changes can happen gradually as needed rather than all at once. This flexibility means the technology investment lasts longer while still meeting evolving demands. Overall, growth becomes easier to manage when the applications can scale properly.
7. Regulatory Compliance
Modernized IBM i applications make it easier to follow industry rules and government regulations. They include features that automatically meet common standards for data handling and security. As a result, companies avoid penalties that come with non-compliance issues. Furthermore, staff spend less time worrying about rules and more time focusing on their actual work. The business maintains its good reputation by consistently meeting all necessary guidelines without struggle.
8. Vendor Support
Modernized IBM i applications continue to receive full support from technology providers. This simply means businesses can get expert help when they need it. As a result, companies avoid the risk of running unsupported technology that becomes difficult to maintain. Furthermore, new features and improvements keep arriving through official channels. This ongoing support gives peace of mind that IBM i applications won’t suddenly become obsolete. Having reliable vendor backing makes the applications safer and more dependable for daily operations.
Summing Up
Modernizing IBM i applications is a smart way to keep your business running smoothly for years to come. Modernizing isn’t just about fixing old problems; it’s about adding new possibilities. Your application can work with newer apps, handle more data, and give your team better tools. The best part? You don’t lose what already works. The key is to take it step by step. Start with what matters most, whether it’s security, speed, or connecting with other tools. Small changes add up over time.
By future-proofing these applications, companies can avoid many common problems before they happen. Businesses that invest in modernization save money over time while keeping their operations efficient and secure.